The original AWSCodeStarFullAccess policy is full [to provide access to AWS CodeStar via the AWS Management Console] yet it still does not grant enough access to create a Code connection for IAM at CodePipeline. So we had to manage to create a custom policy based on AWS tutorial suggestions.
Working CodeStar policy
So based on this post we found out the full statement for CodeStar working policy. See it below:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"codestar-connections:CreateConnection",
"codestar-connections:DeleteConnection",
"codestar-connections:GetConnection",
"codestar-connections:ListConnections",
"codestar-connections:GetInstallationUrl",
"codestar-connections:GetIndividualAccessToken",
"codestar-connections:ListInstallationTargets",
"codestar-connections:StartOAuthHandshake",
"codestar-connections:UpdateConnectionInstallation",
"codestar-connections:UseConnection",
"codestar-connections:TagResource",
"codestar-connections:ListTagsForResource",
"codestar-connections:UntagResource"
],
"Resource": [
"*"
]
}
]How to add it
Now you need to log in as a root user into AWS and go to IAM Management Console.
Here at the left side panel we choose Users or User Groups (our case), select corresponding user/group and switch to the Permissions tab. Here we choose to Add permissions, see below:
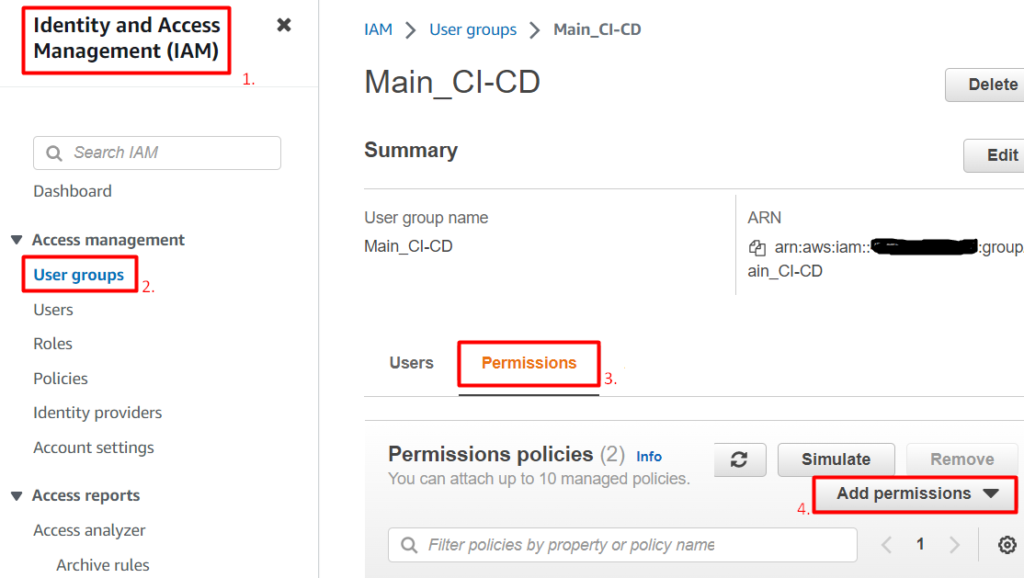
After that we Create inline Policy:

Now we choose the JSON tab and copy/paste a policy of choise from that page into the JSON editor.
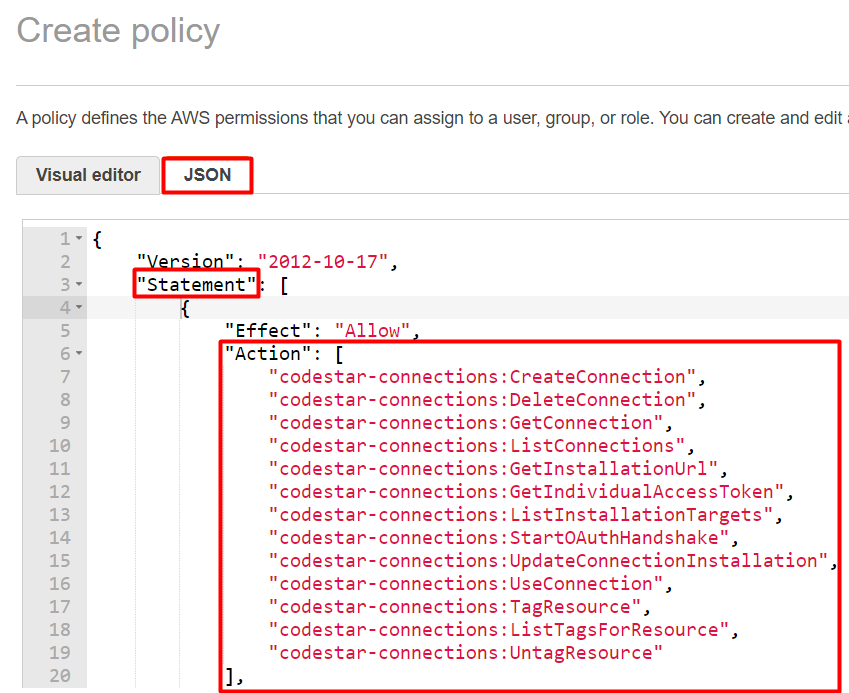
Now we are to review, name and save it. If we navigate to the IAM Policies page we’ll find it there:
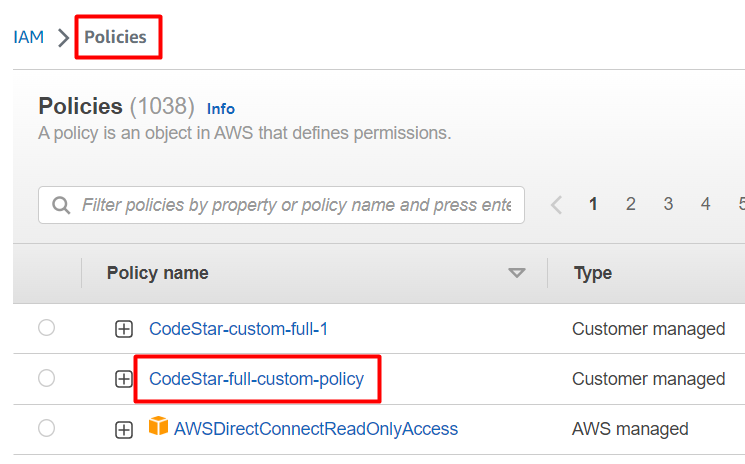
Now we may add it to a user or a user group for the managing Code connections (eg. github) in the CodePipeline creation process.
Note: One may test existing (or new) policies in the Policy symulator.
